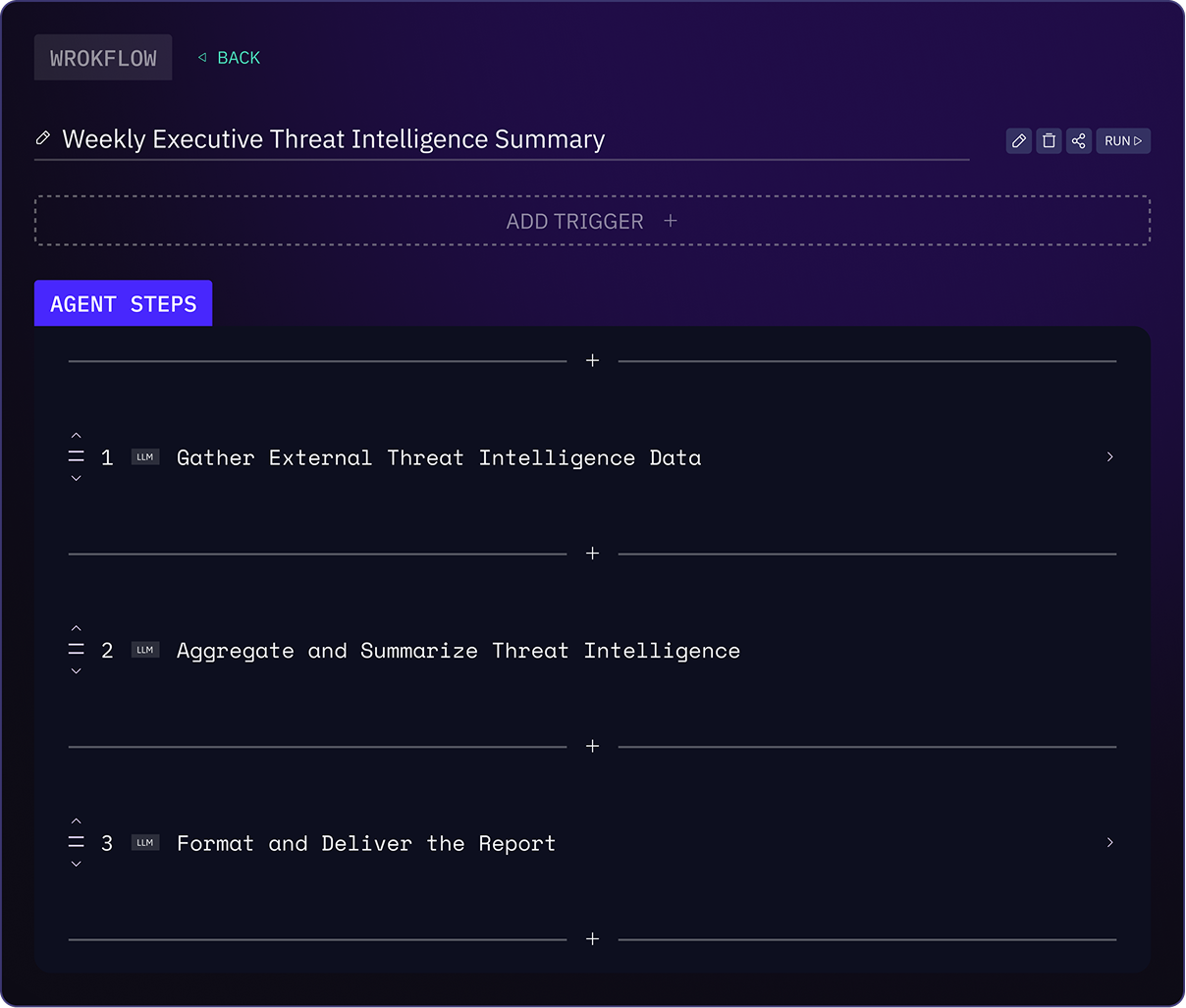
Autonomous Security Operations for Modern SOC Teams
Security Operations Centers weren’t designed for the volume, speed, or autonomy of today’s threats. Analysts are buried under alerts, forced to swivel between disconnected tools, and asked to respond faster than humans realistically can. Kindo gives SOC teams a different operating model.
Instead of managing alerts, your SOC runs on AI-native workflows that correlate incidents, prioritize risk, execute response actions, and verify outcomes from a single execution environment. The result is a SOC that resolves incidents, not just detects them.

Unify Detection, Context, and Response
Traditional SOCs are built on stacks of point tools. SIEMs collect signals. SOAR tools automate fragments of response. EDR and XDR fire alerts. Analysts do the rest. Kindo collapses that complexity into one AI-native control plane.
AI agents continuously ingest alerts, logs, and telemetry across your environment, reason about what actually matters, and take action with full visibility and guardrails. Detection, investigation, response, and verification all happen in the same execution loop.
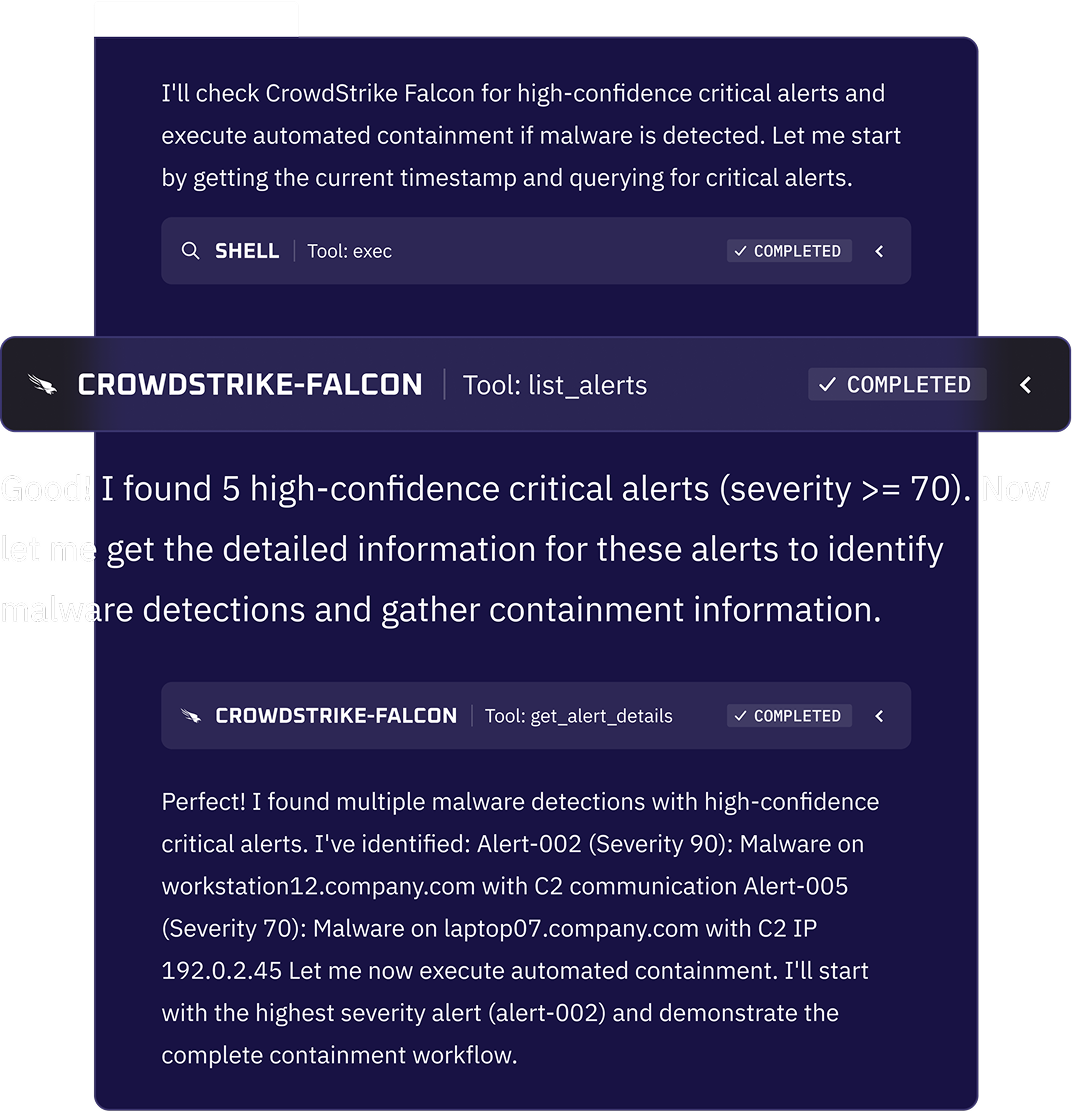
Correlate Incidents Automatically, Not Manually
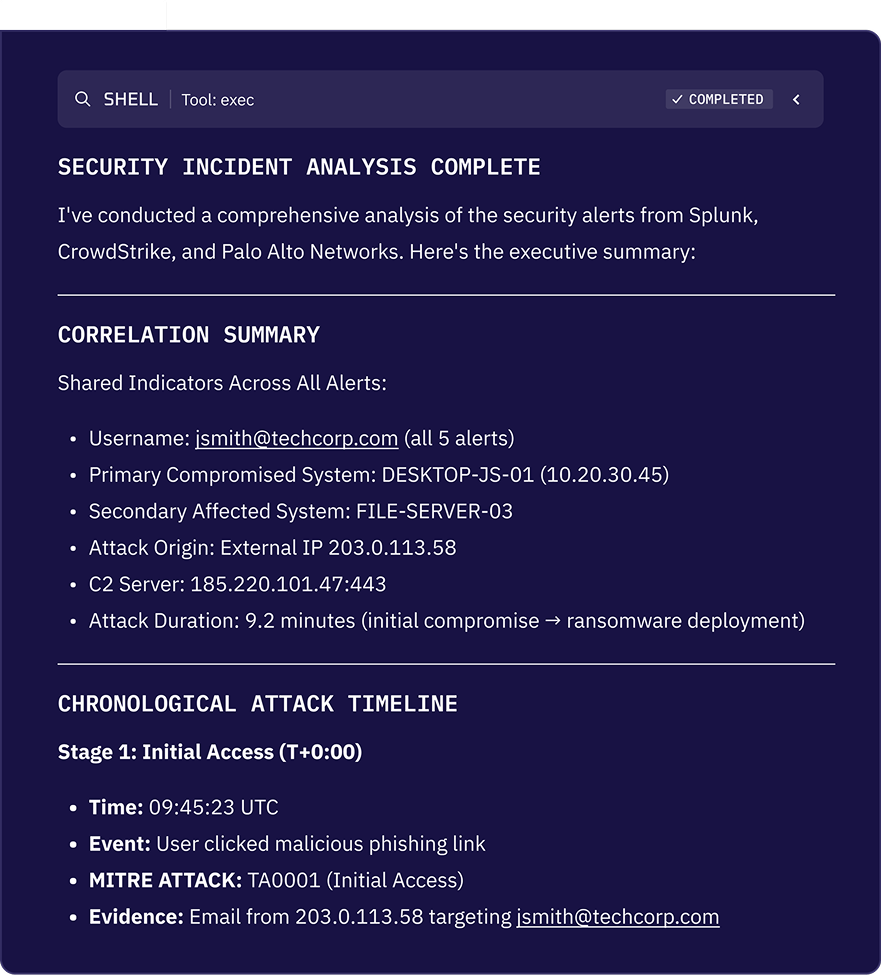
Most SOC time is lost trying to answer one question: What actually happened?
Kindo’s AI agents automatically correlate alerts, logs, identity events, and infrastructure signals into a coherent incident narrative. Related activity is stitched together into a timeline that shows entry point, blast radius, and impact without requiring analysts to manually query multiple tools.Analysts validate and escalate with confidence, backed by a complete picture of the incident and its progression.
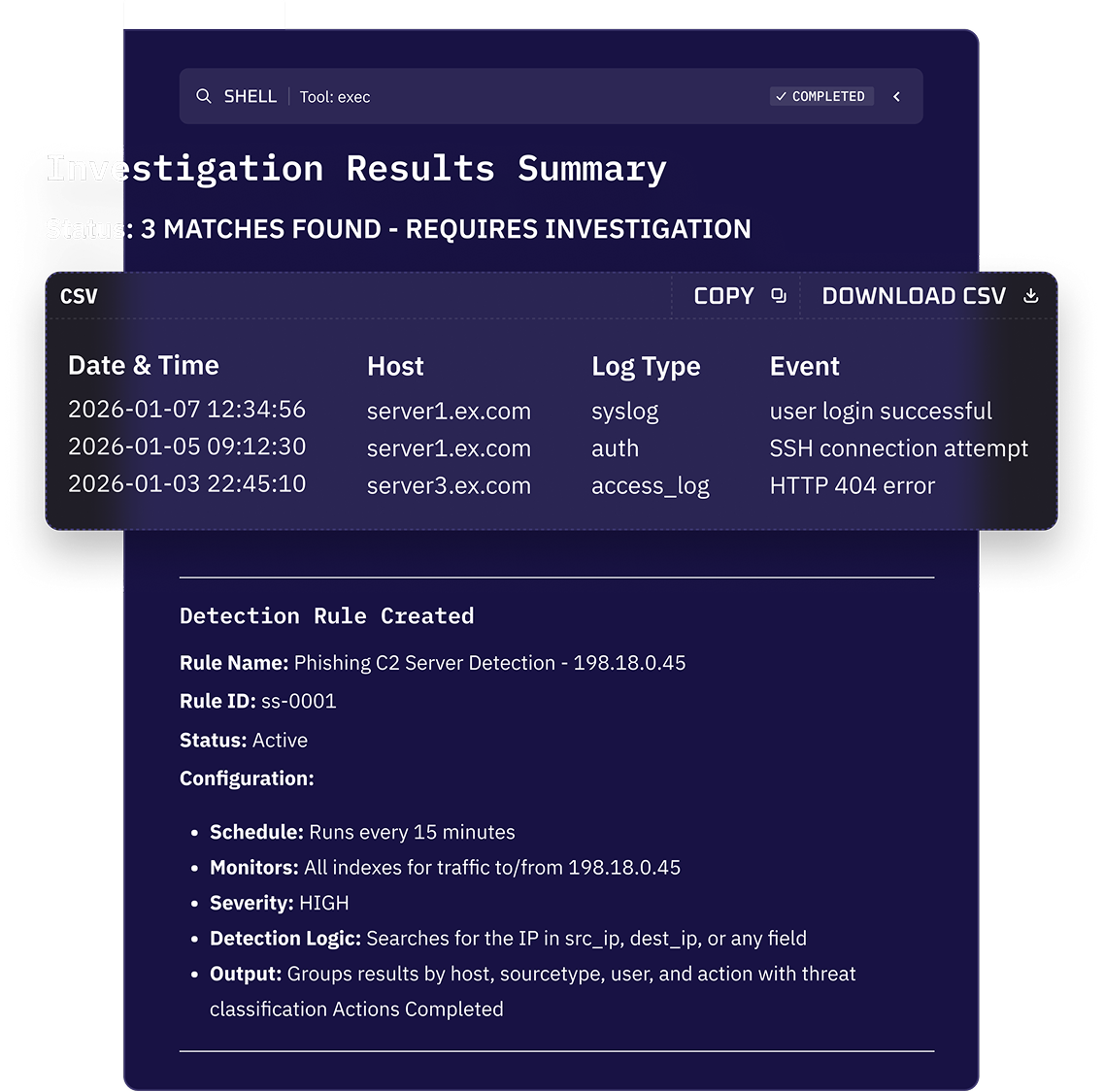
Prioritize Risk in Real Time
Kindo continuously evaluates incoming alerts against real-world context such as asset criticality, identity risk, behavioral anomalies, and threat intelligence. Low-confidence noise is deprioritized or closed automatically. High-risk incidents surface immediately with clear justification.
This isn’t static scoring. The system adapts as your environment and threat landscape change, learning from outcomes and analyst feedback.
Execute Containment Across Your Stack
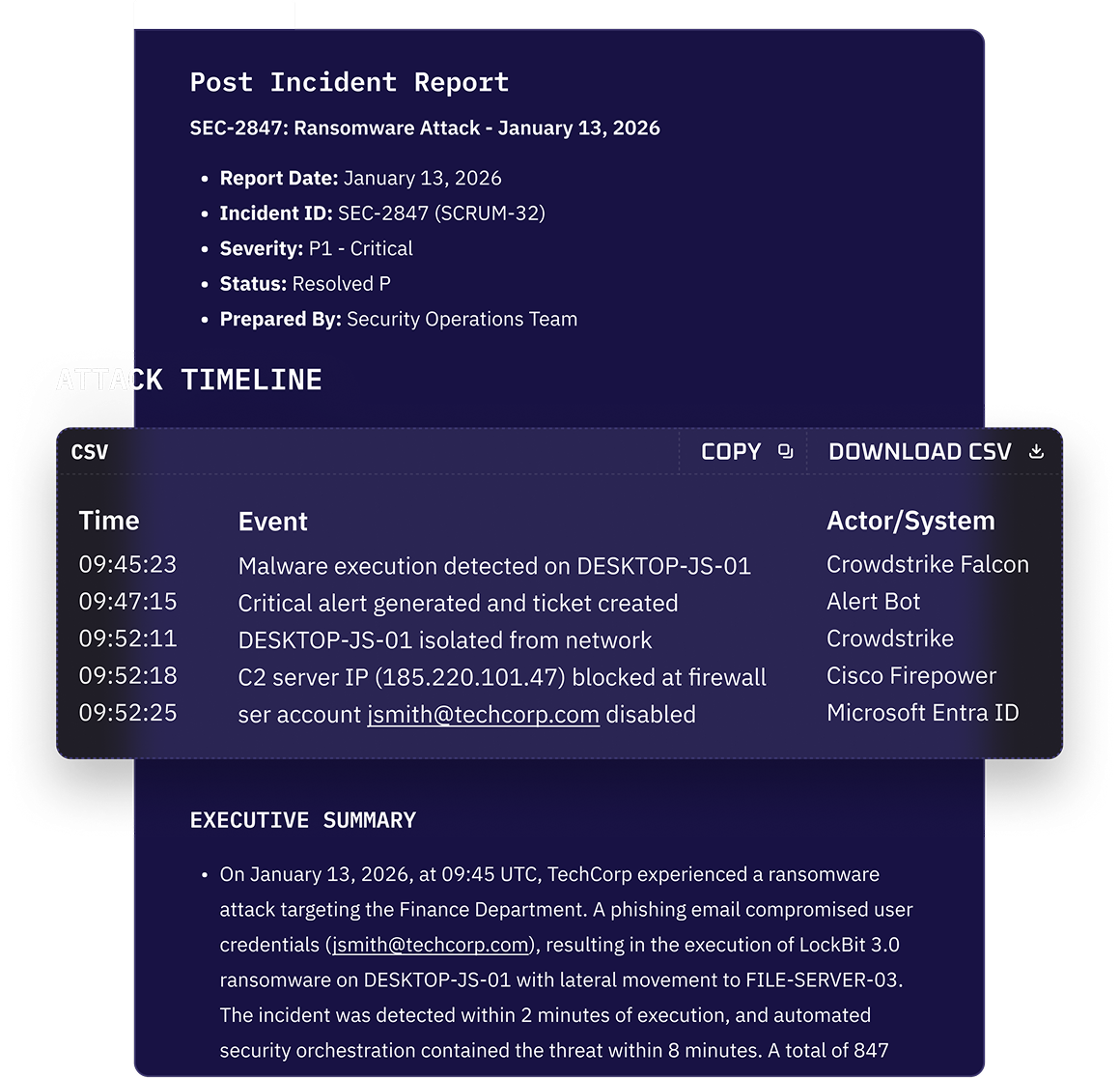
Kindo translates response intent into coordinated action across your security and infrastructure stack. Hosts are isolated, accounts suspended, access paths closed, and malicious activity stopped in seconds, not hours.
Every action is executed with approvals, policy controls, and audit logging intact. Outcomes are verified automatically, so the SOC knows the threat is actually contained.
Continuously Adapt Detection with Live Intelligence
Threat intelligence shouldn’t live in PDFs or feeds that require manual tuning. Kindo continuously ingests and enriches threat intelligence, evaluates relevance to your environment, and adapts detection logic automatically. Indicators that matter are activated quickly. Irrelevant noise is ignored. Detection evolves as attackers do, without adding analyst workload or rule sprawl.