.jpg)
Defending Against AI Powered Cyberattacks in 2025 with Kindo
In our previous blog post we looked at five of the biggest AI powered attacks of 2025, from deepfake driven wire fraud to an all-in-one malware chatbot. Those incidents showed how accessible powerful generative models have become and how quickly attackers adapt.
This follow-up describes how Kindo’s AI powered workflows can help you harden your environment against the same tactics. Each section ties an attack scenario from part 1 to a concrete workflow that Kindo users can implement today.
1. Stop AI Phishing with Automated Threat Intelligence
North Korea’s Kimsuky group demonstrated how a large language model can churn out convincing emails and even fabricate government identification documents. The targets downloaded fake security updates and unwittingly executed obfuscated scripts. Defending against these campaigns goes beyond employee training, it also depends on keeping detection rules current as new indicators of compromise appear.
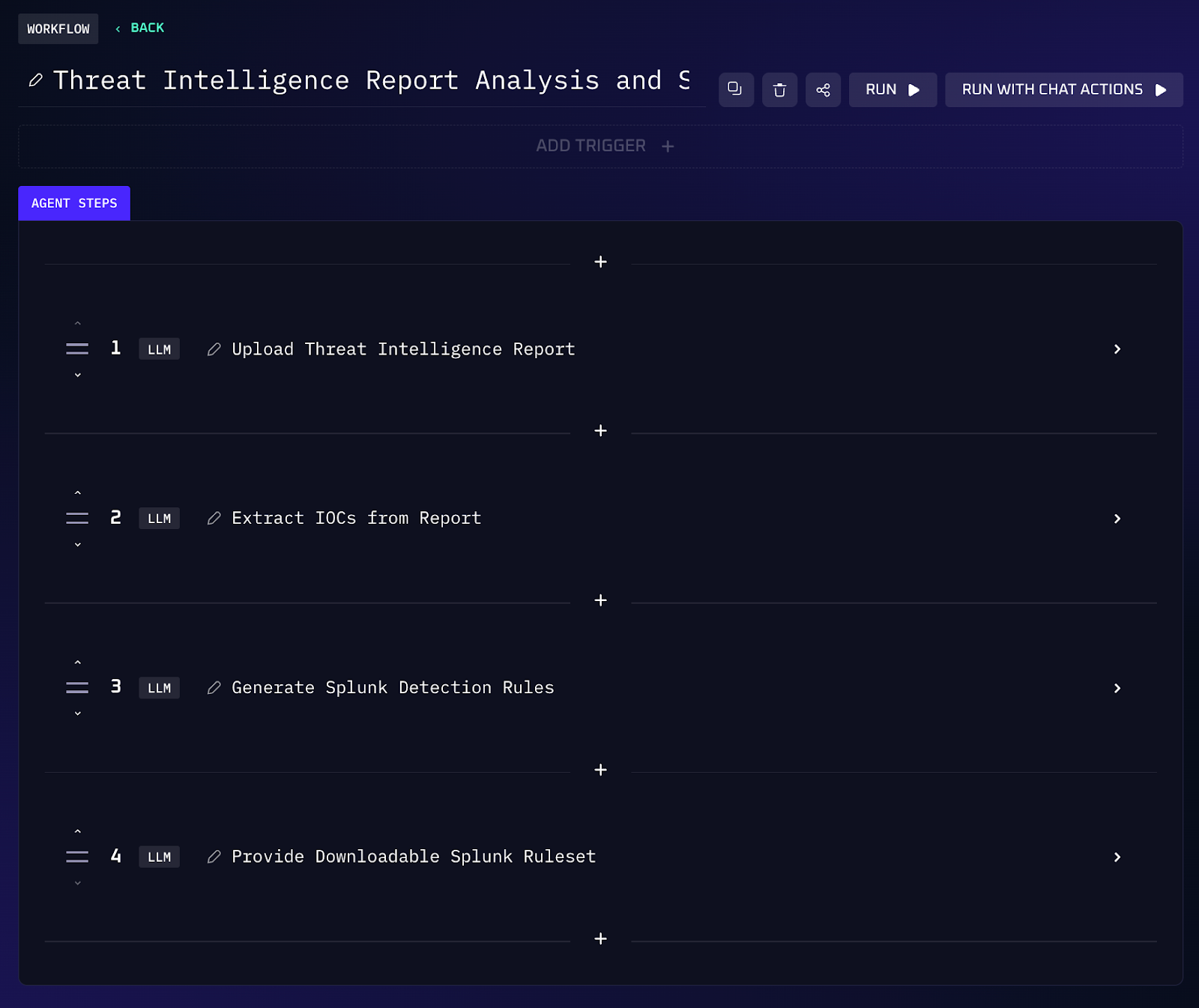
Workflow Steps (Threat Report → Splunk Playbook)
1. Upon receiving a new threat intelligence report, Kindo can analyze the document and extract indicators of compromise.
2. Using these indicators of compromise, Kindo can generate detection rules in Splunk to identify and flag matching emails.
3. The workflow provides the option to either download the rule set or configure it for automatic deployment in Splunk.
Value of Automation
By converting threat intelligence into actionable detections within minutes, you can reduce the mean time to detect (MTTD), minimizing the window of opportunity for AI powered phishing attacks to succeed. Analysts are no longer required to manually input indicators of compromise into dashboards, and the repeatable workflow ensures consistent responses to future alerts.
2. Prevent Deepfake CEO Scams via Identity Checks
Deepfake video calls nearly cost a Singaporean firm US$500,000 when cybercriminals mimicked the voices and faces of its executives. Social engineering can trick even seasoned employees, so the focus must be on hardening the accounts that attackers hope to abuse after the attack. Kindo can use Entra ID and SailPoint integrations (for example) to monitor privileged accounts for risky conditions.
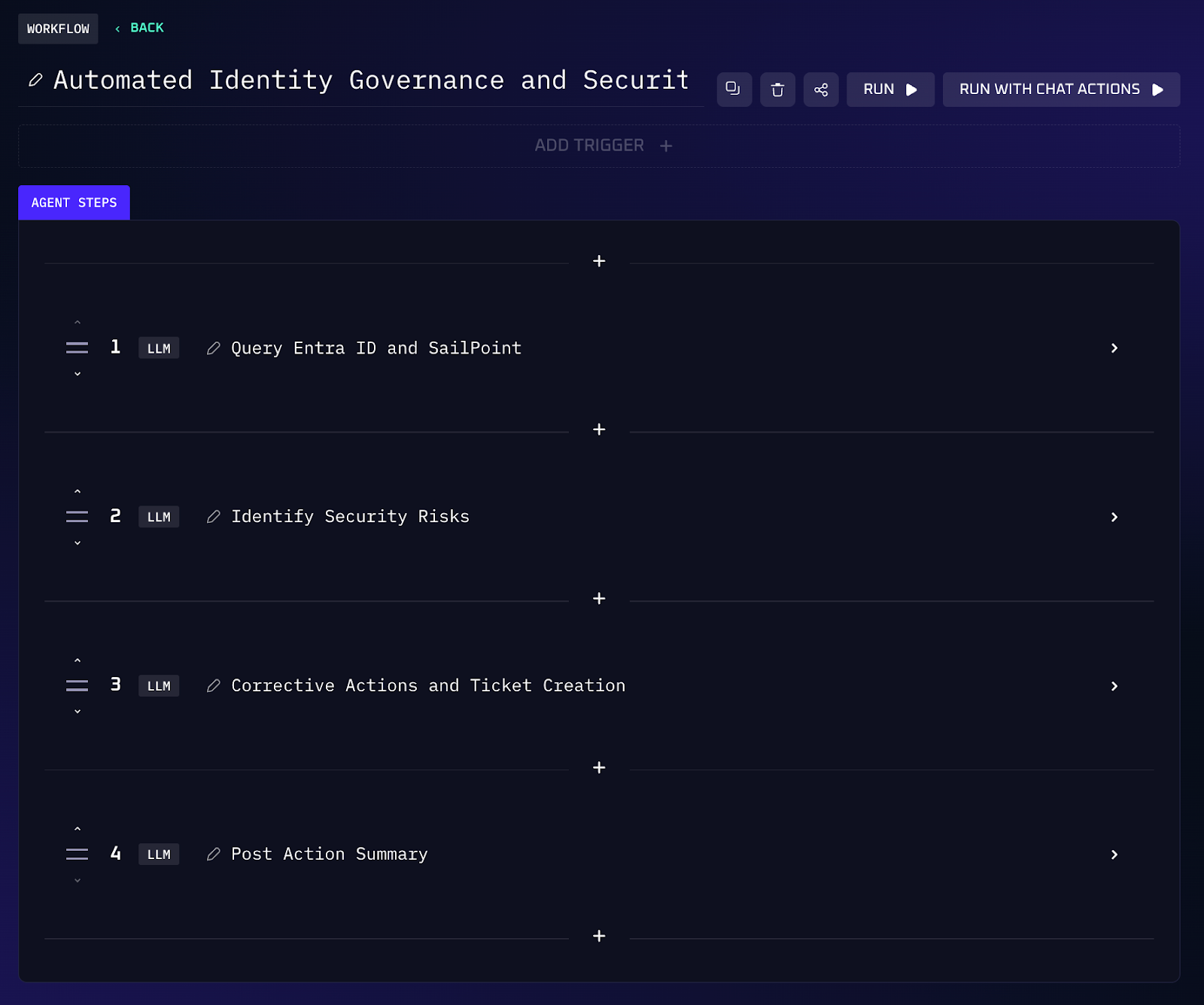
Workflow Steps (Risky User Detection & Response)
1. Kindo reads user records from Entra ID and SailPoint, including role assignments, MFA status and recent login locations.
2. It checks for missing multi-factor authentication, stale high privilege roles, and anomalous sign-ins (e.g., an executive account accessed from a new region).
3. If an account violates policy (like a global admin without MFA), the workflow automatically locks or disables the account until an administrator re-enables it. It can also reset credentials and require MFA enrollment.
4. The agent posts a summary in chat and creates a ticket in your identity governance tool so that the remediation action can be audited.
Value of Automation
Attackers usually rely on compromised or weak accounts to move funds after a successful deepfake call. By constantly checking for gaps like missing MFA or unused privileges, the workflow removes those weak links. Executives can still join video calls, but if someone attempts to misuse their credentials, the account’s protections prevent unauthorized transfers.
3. Find Exposures Before Claude-Assisted Attacks Do
In one 2025 incident, a single attacker used Anthropic’s Claude chatbot to identify vulnerable websites, generate custom malware, and even draft ransom notes. The AI scoured the web for exposed endpoints, sensitive data, etc. Kindo can flip the script: by running your own automated penetration tests, you discover and fix vulnerabilities before an attacker using AI can exploit them.
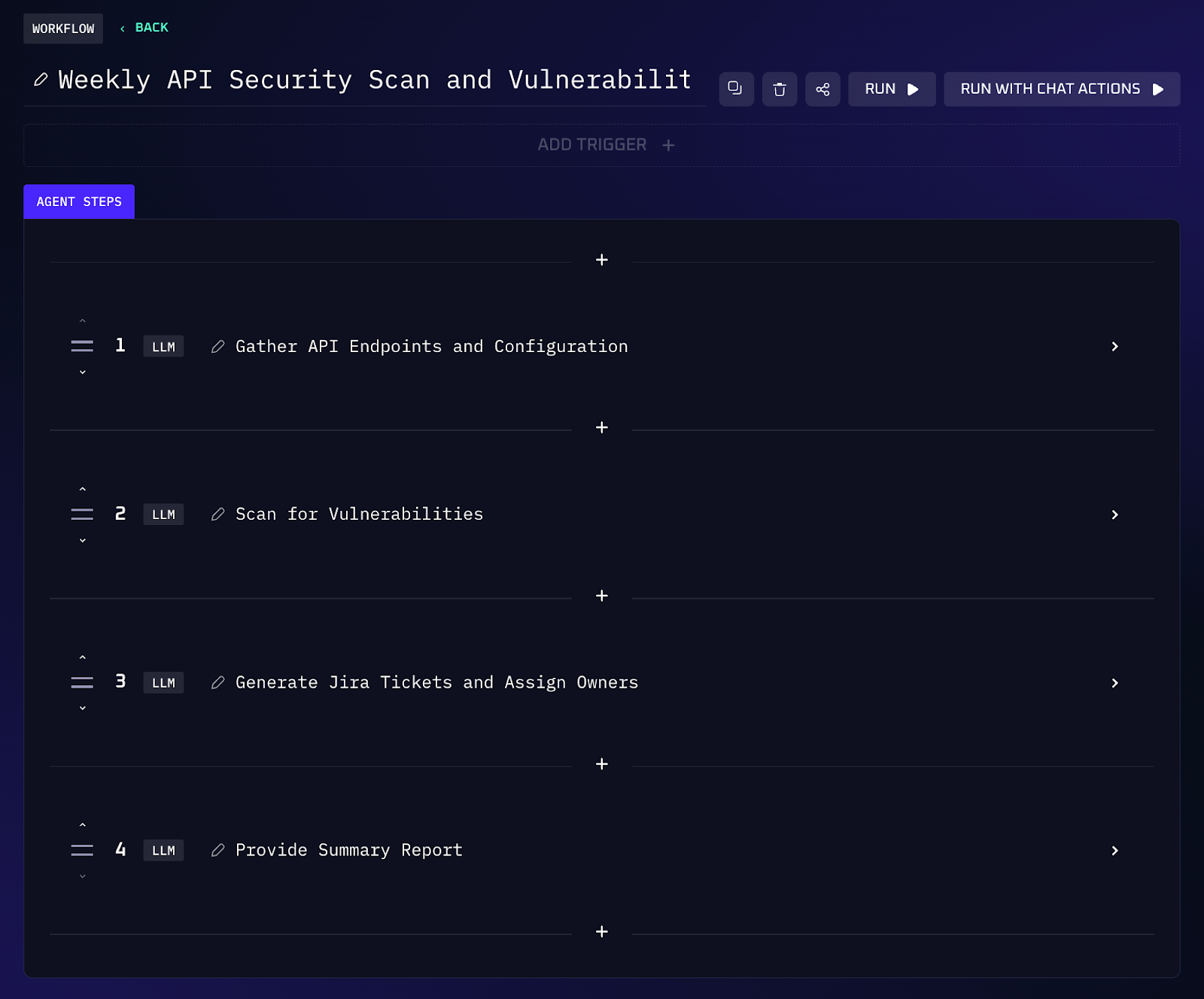
Workflow Steps (Automated Penetration Test & Remediation)
1. Start by specifying the domain or application to assess. The agent maps endpoints, APIs and automation workflows.
2. It then scans for weak authentication, unpatched services, exposed secrets and other misconfigurations, similar to the reconnaissance performed by Claude.
3. Each issue is written to a structured report and logged. The agent groups related issues and prioritizes them based on severity.
4. For every finding, the workflow automatically creates a ticket in your task tracker (e.g. Jira) and assigns it to the appropriate owner.
Value of Automation
Proactive penetration testing reduces the attack surface available to AI enabled cybercriminals. Because the workflow can repeat on a schedule, new exposures are caught soon after they appear. The automatic ticketing also ensures that every issue has an owner and timeline, so nothing slips through the cracks.
4. Block Phishing-as-a-Service Domains Quickly
Darcula phishing-as-a-service (PhaaS) and similar platforms enable cybercriminals to create convincing phishing websites for any brand on demand. By frequently rotating domains, PhaaS providers successfully bypass traditional blocklists. Leveraging threat intelligence feeds, Kindo can automate the identification of new malicious domains and quickly deploy detections.
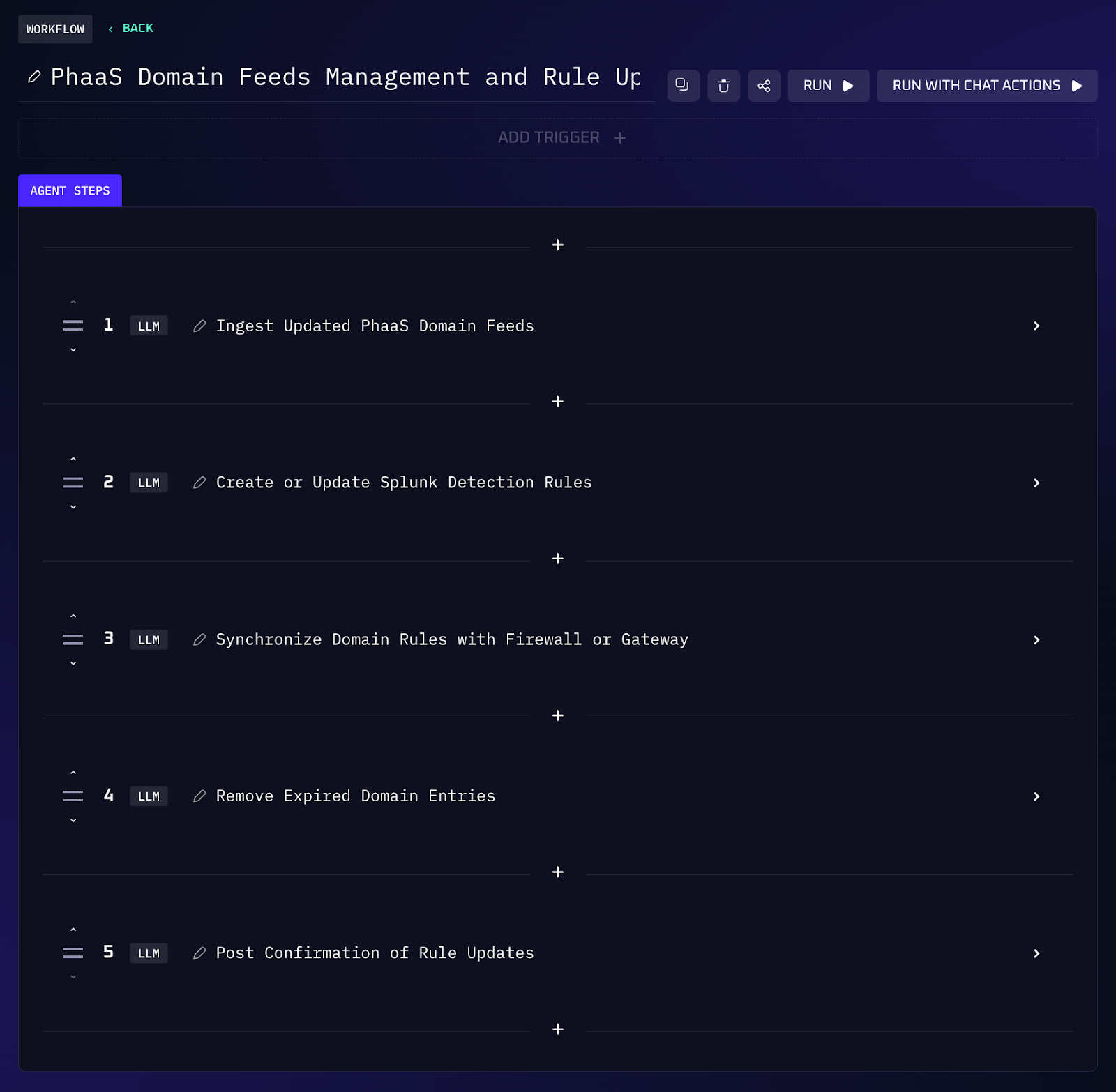
Workflow Steps (PhaaS Feed Ingestion & Detection)
1. The agent monitors and subscribes to the latest threat intelligence feeds, including those related to PhaaS infrastructure and other relevant threats.
2. For each domain or URL, the workflow writes a Splunk rule that flags traffic to those addresses and can trigger actions like blocking or isolating a host.
3. Because these feeds update frequently, the agent reloads them on a scheduled basis, removing expired entries and adding new ones.
4. Optionally, the workflow pushes the updated list to firewalls or secure web gateways to block access preemptively.
Value of Automation
PhaaS succeeds for cybercriminals through leveraging volume and rotation tactics. Relying on manual updates to domain lists is inadequate to keep pace. By automating domain ingestion and rule creation, you can instantly identify new domains as they appear, effectively disrupting the PhaaS operators' business model and protecting your users from fraudulent cloned websites.
5. Respond to AI-Generated Malware with Incident Response
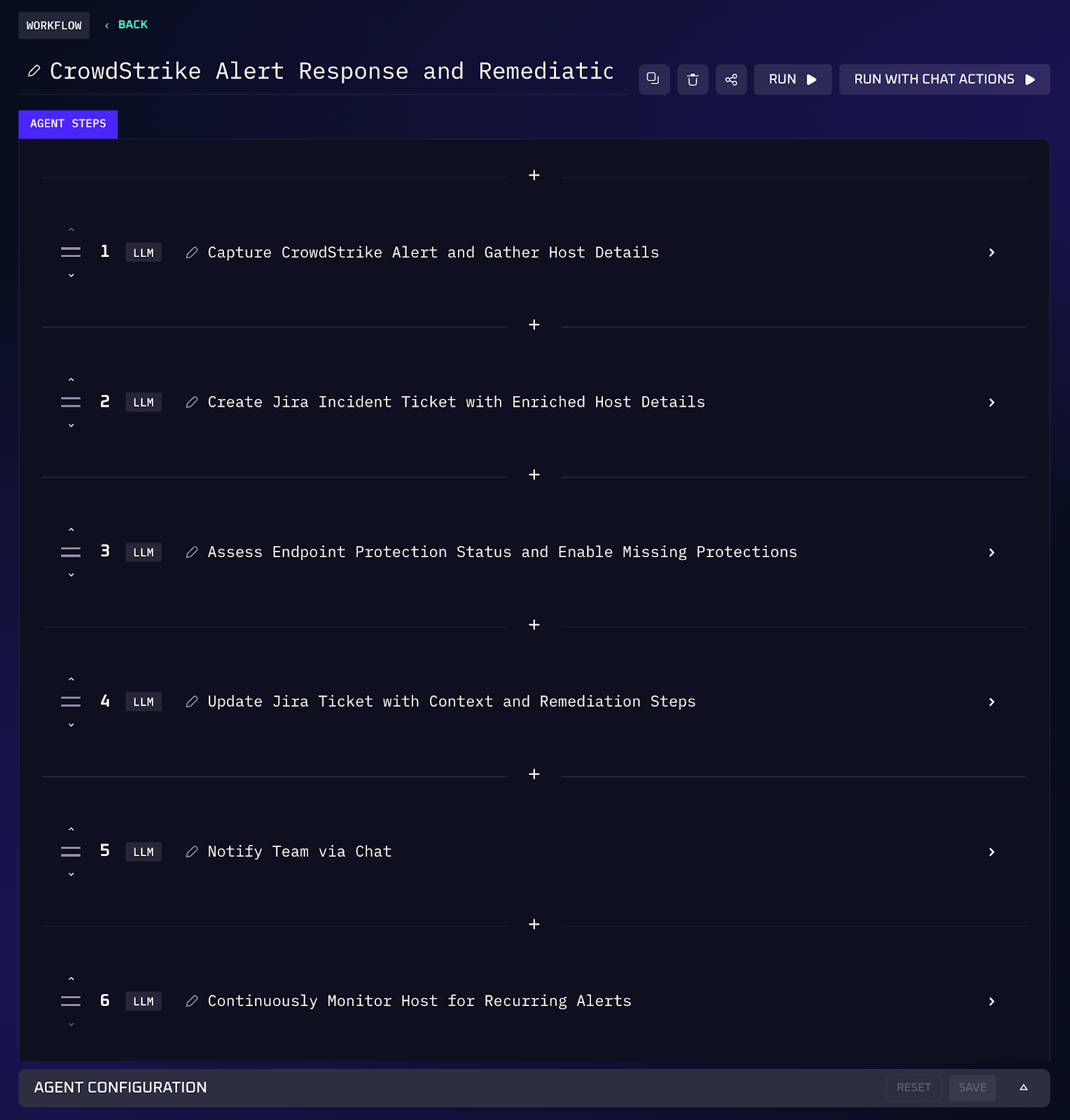
Malicious chatbots like Xanthorox offer a suite of AI modules that can write malware, extract secrets from screenshots and even reason about the best phishing hooks. When a host is hit by this type of malware, speed and context is important. Kindo’s SOC and incident response workflows can enrich alerts from CrowdStrike and automatically strengthen protections.
Workflow Steps (CrowdStrike Alert Enrichment & Hardening)
1. When CrowdStrike detects suspicious behaviour, the agent captures the alert and creates a Jira ticket with a unique identifier.
2. It pulls device details (operating system, running processes) and user information (recent logins, privileged group membership) to add context to the ticket.
3. The workflow compares the alert to recent events to see if it is part of a broader pattern (e.g. multiple hosts exhibiting similar malware signatures).
4. It checks whether endpoint protection features are enabled on the affected host. If protections are missing (for example, ransomware protection or script blocking), the agent turns them on automatically.
5. The agent updates the ticket with remediation steps taken, notifies the responder in chat, and tracks the host for recurrence.
Value of Automation
This workflow guarantees quick enrichment and response to security alerts. With automatic policy enforcement, other hosts in your environment receive better protection, minimizing the likelihood of a similar payload executing successfully in the future. All actions are recorded in a ticket as well, enabling auditors to confirm consistent handling of each incident.
Fight Back Against AI Cybercrime Using Kindo’s Agents
In part 1 of this series we looked at attacks that stood out not just for their creativity, but for the way attackers leaned heavily on AI automation. Trying to counter that manually is an uphill battle, which is why Kindo gives your team its own AI powered edge.
With Kindo’s workflows, you can analyze reports, monitor identity health, run penetration tests, process threat feeds, and strengthen alerts, all without leaving a single interface. Everything happens through a conversational workflow, so the process stays transparent and consistent from start to finish.
The result is that security and operations teams spend less time chasing scattered tools and more time staying a step ahead of AI powered threats. Want to see it in practice? Book a demo and watch these workflows in action.



