.png)
A Guide to AI-Powered Risk & Compliance Workflows (Q4 2025)
Governance, risk, and compliance (GRC) work typically depends on accurate data, but most of that data resides across separate systems. Analysts spend their time pulling logs, checking spreadsheets, reviewing scanner outputs, and updating reports. This slows down audits, increases the chance of mistakes, and leaves teams reacting instead of getting ahead of issues.
Kindo gives GRC teams a way to run these tasks through a single conversational interface. Artificial intelligence (AI) pulls data, checks controls, and completes the steps behind the scenes. The result is faster reviews, consistent evidence, and fewer manual steps. Below are five examples of GRC workflows that become more reliable and easier to manage when automated.
1. Continuous Control Monitoring (NIST 800-53 Compliance)
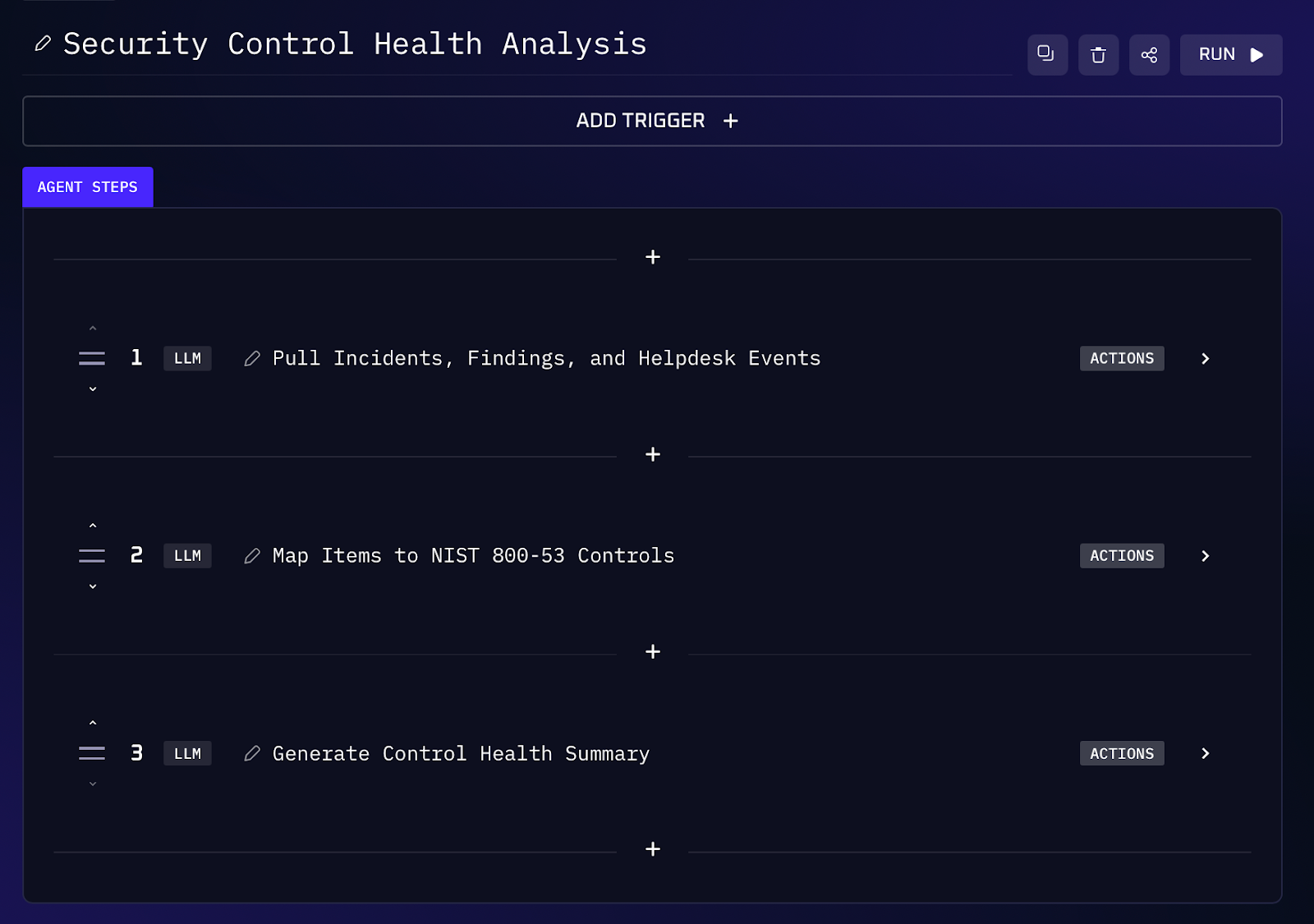
When managing dozens of security controls, compliance teams regularly collect evidence (vulnerability scans, ticket logs, etc.) to assess if controls are operating effectively. In a traditional workflow, you might manually review weekly scanner reports and help desk tickets, then map each issue to relevant controls. Finally, you’d summarize the control health in a spreadsheet or slide deck with red/yellow/green statuses. This process is slow and error prone. AI workflows can act like a continuous controls monitor, automatically aggregating evidence and evaluating control effectiveness. The AI will scan logs, map issues to the corresponding NIST control IDs, and produce a traffic light report of control health for each domain.
Workflow Steps (Control Evidence Aggregation)
1. The AI agent connects to source systems (e.g. Jira for incident tickets, Nessus or another scanner for vuln reports) and pulls raw logs for the period of interest. It compiles entries like open incidents, failed checks, or unresolved vulnerabilities.
2. Using a control framework knowledge base, the AI matches each log entry to relevant controls. For instance, an unresolved critical vulnerability would be tagged under RA-5 (Vulnerability Scanning), while an overdue incident response might fall under IR-4 (Incident Handling). Repeated helpdesk issues about access could relate to AC-2 (User Access Management), etc.
3. For each control family or key control, the agent determines if requirements were met or missed based on the evidence. It then produces a red / yellow / green status for each area.
Value of Automation
By automatically analyzing evidence logs and mapping them to controls, compliance officers get real time visibility into control effectiveness. This control monitoring approach can optimize audits and outcomes, providing real time assessment, analysis, and reporting about the status of the organization’s security controls. In seconds, the team sees which controls are healthy and which need attention, without wading through spreadsheets. This not only reduces audit preparation time (no more manually compiling control evidence for weekly meetings) but also catches compliance gaps early. Instead of reactive, point-in-time checks, GRC can move to a proactive stance where an AI assistant flags control weaknesses continuously, reducing the chance of surprises during formal audits.
2. DORA ICT Asset Inventory Completeness Check
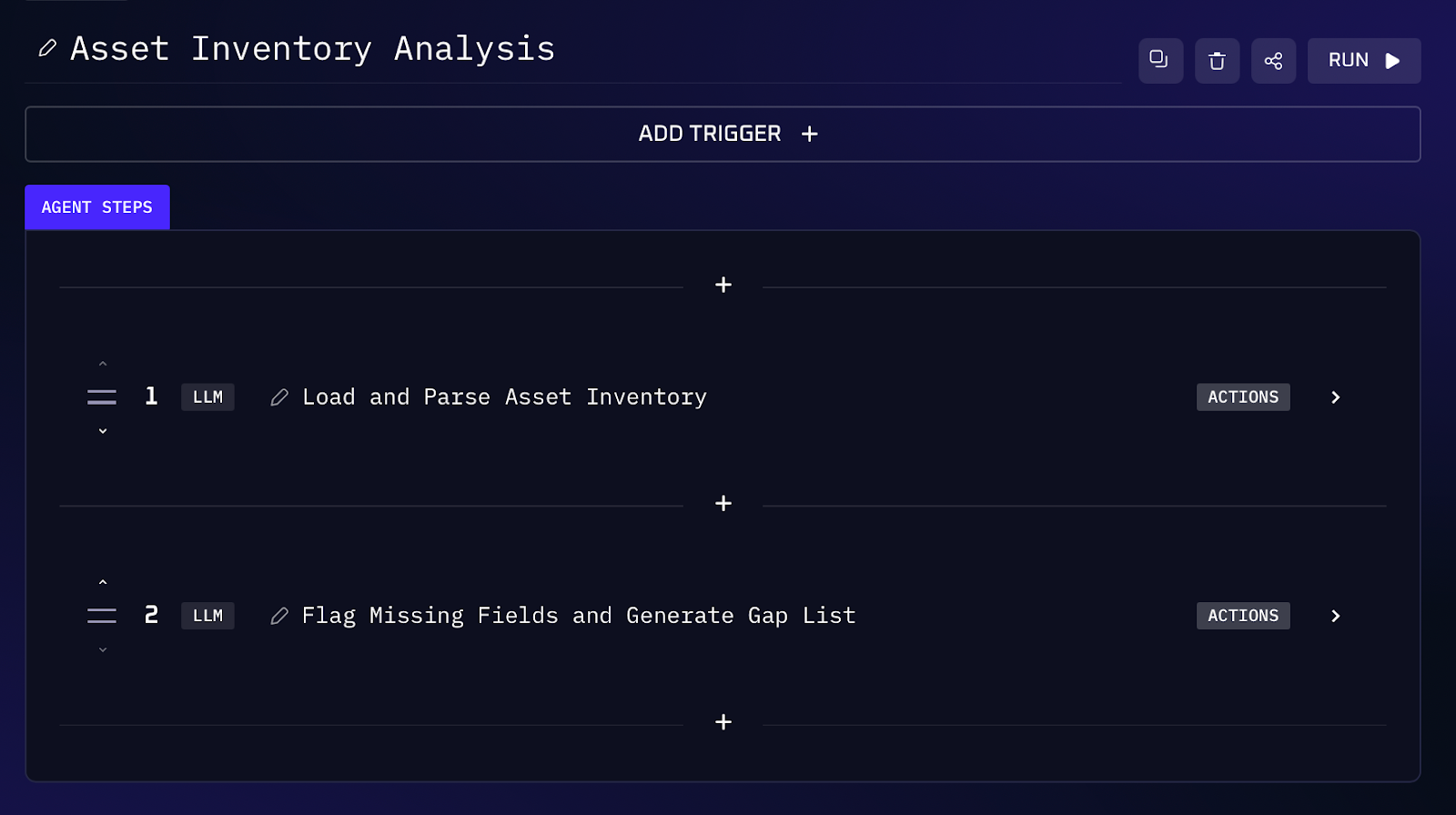
Some entities under the EU’s Digital Operational Resilience Act (DORA) must maintain a detailed inventory of their IT systems, especially those supporting important business functions. In practice, this means tracking every application, database, server, etc., and ensuring key metadata is documented, like the business function it supports, an owner, recovery plans, and risk classification. Performing an inventory completeness check by hand is cumbersome: you’d audit the CMDB or spreadsheet line by line against DORA’s requirements. An AI workflow can quickly review your asset inventory for gaps. The assistant will parse your asset list, identify which systems are marked as supporting critical/important functions, and then verify if required details are present for each.
Workflow Steps (DORA Asset Audit)
1. The AI workflow takes your asset registry (e.g. a spreadsheet export) as input. It reads each entry: system name, description, whether it’s tied to a critical business function, and all recorded attributes (owner, backup info, risk rating, etc.).
2. Using DORA guidelines, the AI flags which assets are supporting important functions (this might be explicitly tagged in your data, or inferred from keywords). For those assets, it checks that all mandated metadata is present. For example, DORA expects organizations to “map those [assets] considered critical, including their configurations, interdependencies” and have continuity plans for them. The agent verifies fields like service owner, backup or continuity plan, and risk level are filled in. It also notes any obvious omissions for non critical assets (e.g. missing classification might still be worth flagging).
3. The output is a list of any missing or incomplete fields per asset. For instance: “CRM Database: missing data owner; Payroll System: no backup plan documented”. The agent also tells you if any critical function asset was entirely absent from the inventory (a serious gap). In addition, it can summarize coverage: e.g. “Out of 120 assets, 35 support critical functions. All critical assets have an owner and risk rating; 5 lack documented recovery plans.” This provides a clear checklist of remediation steps to achieve full DORA compliance on asset inventory.
Value of Automation
This automated check spares GRC teams from painstaking manual reviews of asset lists. It ensures that no system falls through the cracks, especially those underpinning vital services. By tagging assets linked to critical functions and pinpointing missing details, the AI reduces the risk of non compliance with DORA’s strict ICT asset management rules. Instead of combing through Excel filters, compliance leads get an instant report of gaps to address. This not only accelerates DORA readiness but also improves resilience, you know every critical system has an owner, a recovery plan, and a risk assessment on file.
3. Weekly Vendor Risk Monitoring
Third party risk management is an ongoing challenge, today’s vendors might be tomorrow’s breach cause. Security ratings platforms like BitSight scan vendors’ external cyber posture and assign grades (like A, B, C) based on factors such as exposed systems, patching cadence, and known compromises. In a manual process, a risk analyst might log into BitSight weekly, note any score drops or new alerts for key vendors, and then update a report or send emails if a partner’s rating falls below a threshold. A workflow can automate this oversight. The AI agent will fetch the latest ratings via API, compare to historical data, and give you an organized update for all your suppliers.
Workflow Steps (Continuous Vendor Risk Check)
1. The agent calls the BitSight (or similar) API for each vendor on your watchlist (e.g. important SaaS providers, cloud hosts, payment processors). It obtains the current security rating (e.g. 720 out of 900, or letter grade) and possibly the breakdown by risk categories.
2. The AI compares this week’s rating and category scores to last week’s data (which it can store or you provide). It notes any significant drops in overall score or any category going from good to poor. It also detects new risk indicators - e.g. a first time appearance of a malware infection or a major spike in exposed credentials reported.
3. Based on the changes, the agent assigns a simple status: green for vendors with stable or improving scores (no action needed), yellow for minor fluctuations or warnings (a small score drop or one new moderate finding), and red for large degradation or persistently low ratings.

Value of Automation
This weekly vendor risk digest means no more manual polling of dashboards or overlooking a brewing vendor issue. The AI monitors your third parties in the background and surfaces only what’s important. This gives early warning on third party cyber issues so you can act (reach out to the vendor, escalate internally) before a small issue becomes a big incident. It also maintains a historical trail of vendor security health mapped to standards like NIST or ISO, which is useful for audits and due diligence.
4. High-Risk SaaS Usage Tracker
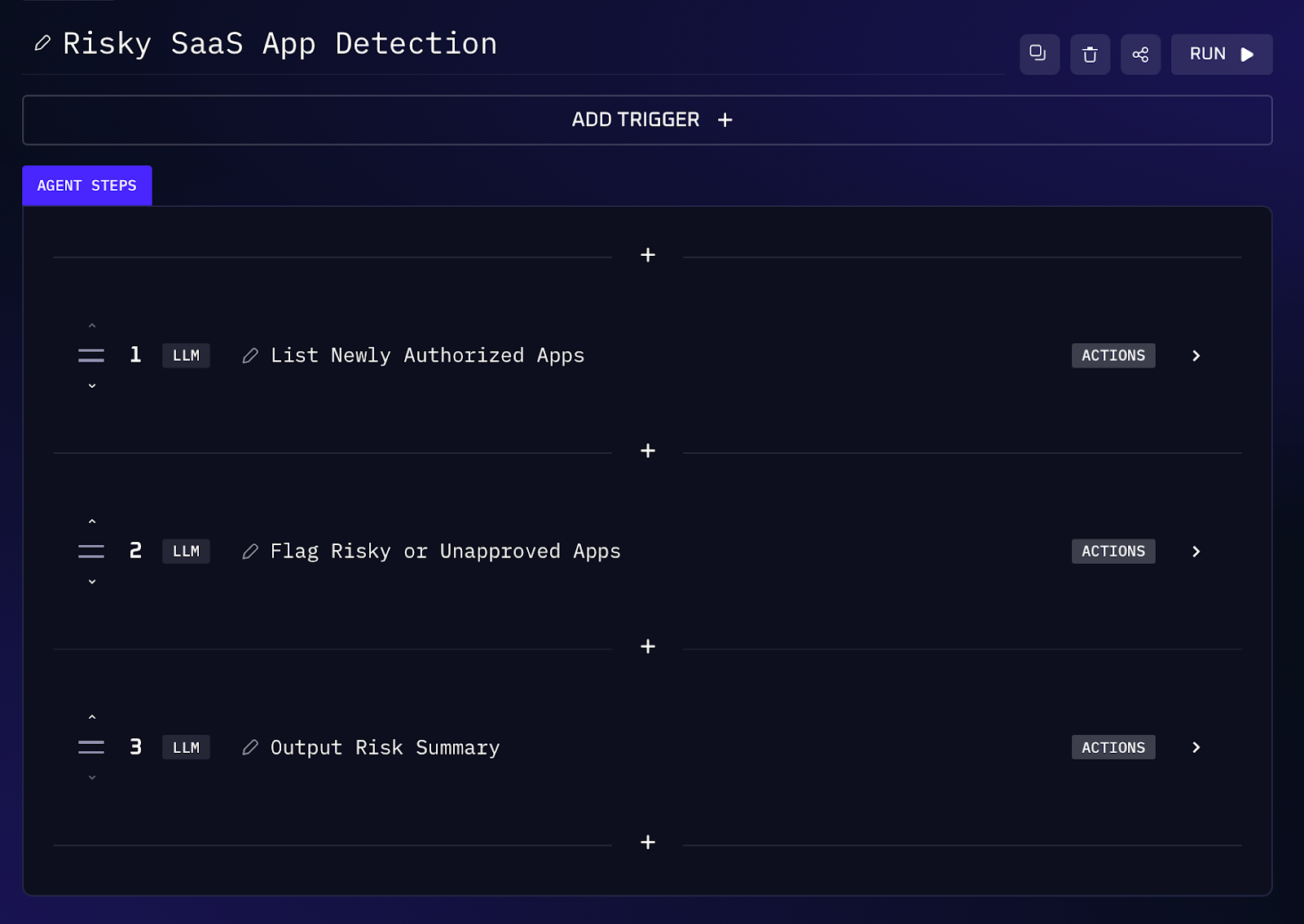
With the explosion of SaaS apps and cloud services, employees often connect third party apps to company systems via OAuth or single sign on (think Slack plugins, Google Workspace add-ons, personal productivity tools, AI assistants, etc.). Many of these apps fly under IT’s radar - basically classic shadow IT. They might have overly broad permissions (like reading all your Drive files) or come from unknown vendors, posing security and compliance risks. This high risk SaaS tracker workflow helps shine a light on these connected apps. The AI will use the identity providers’ logs and APIs to discover what’s been authorized and assess each app’s risk profile.
Workflow Steps (Shadow IT Discovery)
1. The agent interfaces with your identity/OAuth providers (e.g. Google Workspace admin APIs, Okta system logs) to retrieve a list of all third party apps that users have granted access to. This includes data like app name, the scopes/permissions granted (e.g. “read Gmail”, “access Drive”), the user who approved it, and when it was first seen.
2. It filters for newly authorized apps since the last check (e.g. apps added in the past week), and also any that are infrequently used or never formally reviewed by IT. Newly connected apps are important because they expand your attack surface unexpectedly. The agent might cross check against a whitelist of approved apps; those not on the list are shadow additions.
3. For each app, the AI evaluates risk factors, it flags high risk scopes - for instance, if an app can read or delete files (which maps to sensitive data access), or if it has broad admin privileges. It flags unknown vendors (perhaps comparing the app’s publisher name against known reputable vendors). It also notes if no internal owner is listed (no one accountable for its use). These flags are mapped to relevant controls: e.g. excessive permissions and unvetted software relate to NIST AC-19 (controlling mobile/remote access) and SI-4 (monitoring for unauthorized software), or to ISO 27001 controls on network access and information exchange (Annex A.13).
4. The result is a weekly (or monthly) summary listing any risky apps discovered. The assistant can provide recommendations like “consider revoking or reviewing access for high risk apps.” This report can be delivered in chat or even used to automatically create tickets for IT to follow up.
Value of Automation
This workflow gives security and IT teams full visibility into the shadow SaaS integration ecosystem. By catching new app connections and evaluating their risk instantly, organizations can clamp down on unauthorized data access before it’s too late. In compliance terms, it helps enforce policies that require controlling use of external systems and monitoring for unauthorized connections (a principle in frameworks like NIST 800-53 SI-4). Instead of waiting for a quarterly review or worse, a security incident to discover a rogue app, the team gets an automated watch on SaaS usage. Finally, from an audit perspective, you can demonstrate a process for managing third party app risk (mapping to controls such as access management and supplier security in ISO 27001).
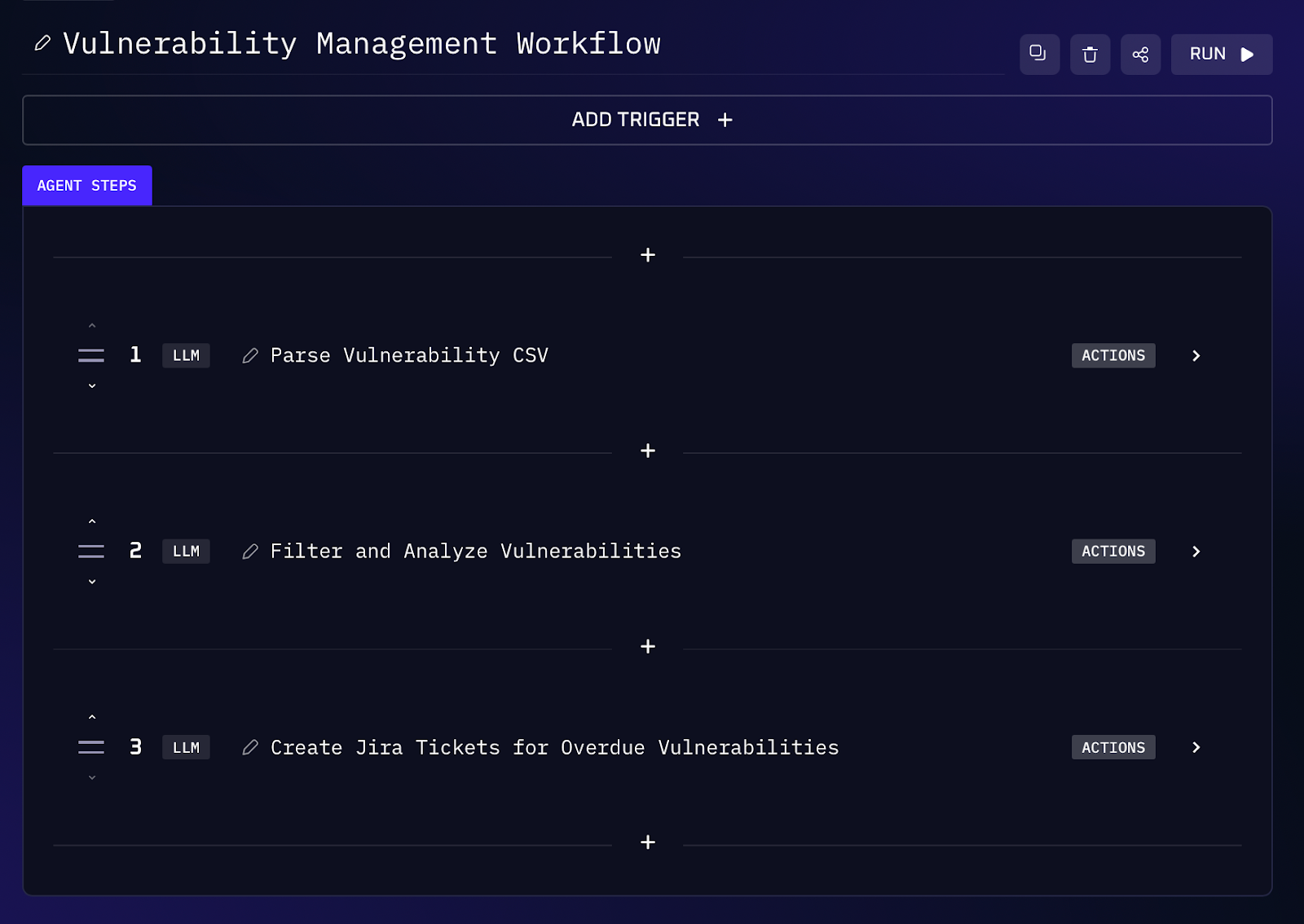
5. Vulnerability Remediation SLA Compliance Check
Even the strongest vulnerability management program can falter if issues slip past their due dates. Many organizations set strict SLAs (service level agreements) for fixing high severity vulnerabilities - often 30 days for highs and sooner for criticals. If a critical CVE isn’t patched in time, it not only increases risk but also creates compliance headaches (auditors will flag missed remediation timelines). This AI workflow acts as a safety net to catch and escalate any overdue vulnerabilities. The agent will parse the scan results, find high/critical vulns past the 30 day window, and automatically generate tickets to ensure they get attention.
Workflow Steps (Vuln SLA Enforcement)
1. The agent reads the CSV or vulnerability report, focusing on each finding’s CVSS score, discovery date, affected asset, and description. It filters CVSS > 7.0 (which covers high and critical vulnerabilities under common scoring definitions).
2. For each high severity finding, it calculates the age (today’s date minus discovery date). Any that exceed 30 days are marked as overdue for remediation (assuming a 30 day SLA is the policy). For example, if CVE-2025-12345 (score 8.0) on Server1 was first found 45 days ago and is still open, that’s a candidate.
3. Using the Jira integration, the AI creates a new issue for each overdue vulnerability. The ticket can be assigned to the appropriate team automatically if desired (e.g. based on asset ownership or a default security backlog).
4. After ticket creation, the assistant returns a list of all the tickets it made, possibly with links or IDs.
Value of Automation
This workflow closes the loop on vulnerability management. It guarantees that serious issues don’t languish unaddressed simply because someone missed an email or spreadsheet entry. By programmatically enforcing the remediate high risk vulnerabilities within 30 days best practice, the organization stays on top of its remediation SLAs. Many standards and regulators (from PCI DSS to FedRAMP) explicitly require timely patching of critical vulnerabilities. An auditor can now see a process in place: any overdue item is escalated via ticket, with a documented trail of who’s fixing it and when.
Move Towards Conversational GRC Operations
The future of compliance operations is looking more and more autonomous and conversational. By using smart AI workflows for tasks like the ones above, organizations can drastically cut down on manual effort, improve accuracy, and respond to risks faster.
Get a demo of Kindo, or visit Kindo.ai learn more about bringing these AI powered workflows to your own risk and compliance processes. The era of waiting on spreadsheets and scattered tools is ending, with conversational GRC automation, staying compliant becomes a much smoother ride.



