
5 AI Driven Threat Intelligence Workflows (Q4 2025)
Security teams in 2025 are inundated with threat data, suspicious IP addresses, domains, ransomware news, and more. Manually gathering and correlating this information from multiple tools can be slow and error prone. The good news is that AI powered automation (like Kindo’s chat-based actions) can cut through the noise, aggregating intelligence from many sources and presenting what matters in seconds.
In this post, we show you five threat intelligence workflows that security engineers can optimize with AI. Each workflow takes a time consuming task, from enriching an IP address to monitoring ransomware leaks, and turns it into an efficient, automated process. The result is faster investigations, proactive awareness, and less context switching for your SecOps team.
1. IP Address Enrichment & Prioritization
When a suspicious IP address pops up in an alert, analysts traditionally have to pivot across multiple sites to find context, checking its reputation on VirusTotal, looking up abuse reports on AbuseIPDB, querying WHOIS for ownership, etc. This workflow automates all those lookups and consolidates the results. It enriches the IP with reputation scores, ASN (Autonomous System Number) and ISP info, and geolocation details from trusted intelligence sources. All that data is then used to calculate a risk score for the IP and determine if it’s likely malicious. By aggregating multi-source context and scoring each IP, the team can immediately see which indicators are high risk. This dramatically reduces manual lookup time, since the highest-risk IPs surface first with all the relevant details attached.
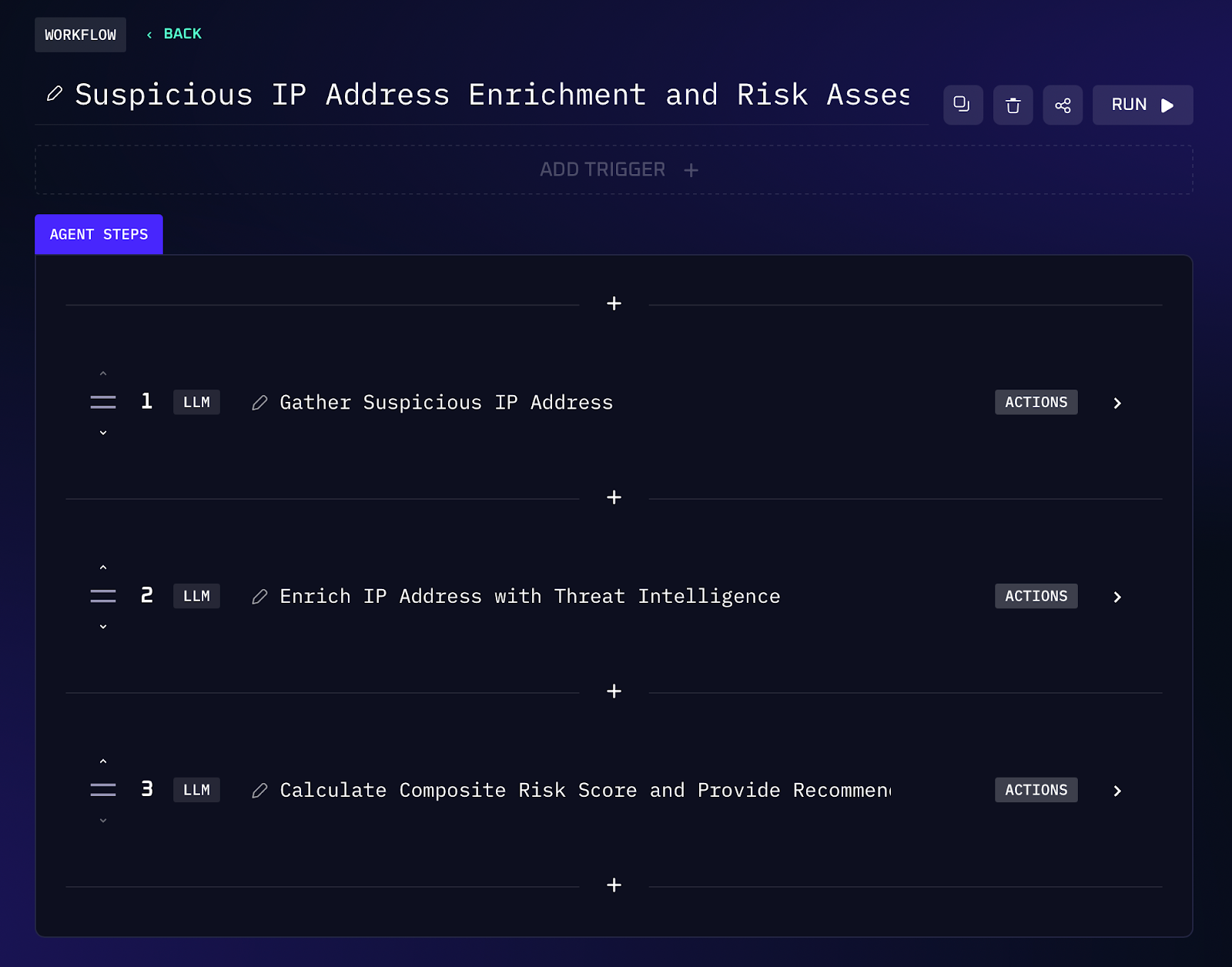
Workflow Steps (IP Enrichment & Scoring)
1. The process kicks off when an analyst provides an IP (from an alert or threat feed) or an alert triggers the workflow with a suspicious IP address.
2. The IP is automatically looked up on services like VirusTotal and AbuseIPDB via their APIs. The workflow pulls reputation data (malicious vs. benign reports) from these sources, and also fetches WHOIS records for ownership and registration details.
3. The workflow aggregates additional context such as the IP’s ASN (which network/block it belongs to) and geolocation (country/region). These details help analysts assess if an IP is out of place (e.g. an admin login from an unusual country or a known hostile ISP).
4. Using the collected intelligence, the AI assigns a composite risk score to the IP. For example, a high score might be given if VirusTotal shows many malware associations and AbuseIPDB has multiple abuse reports. The scoring logic can weigh factors like blacklist presence, recent malicious activity, and whether the ASN is associated with threat actors.
5. The enriched data and score are output for the team. High risk IP addresses are flagged for immediate investigation or even automatically blocked, while low risk ones can be deprioritized. The result is a prioritized list of IP indicators, with the worst offenders at the top.
Value of Automation
By automating IP enrichment, analysts get fast answers without juggling tools. Instead of manually copying an IP into various websites (a time consuming process), the enrichment bot delivers a consolidated report in one go. This not only saves time but ensures no key detail is missed, the workflow consistently pulls the same set of intelligence every time. Surfacing the most suspicious IPs first means the team can focus on what’s truly dangerous instead of wading through benign addresses.
2. Domain Reputation Check (URLscan + Spamhaus)
Analyzing a potentially malicious domain is another common task that benefits from AI orchestration. This workflow takes a user provided domain (for example, one seen in a phishing email or web traffic) and instantly checks its reputation through two lenses: a live website scan and a threat intelligence blacklist. First, it uses URLscan.io to scan the domain, fetching details like the page screenshot, scripts and resources loaded, and hosting information, essentially profiling what the website does. Next, it queries Spamhaus (a renowned threat intelligence provider) to see if the domain or its hosting IP appears on any spam or malware blocklists. By merging the scan results with the blacklist status, the workflow can produce a clear verdict on the domain’s reputation.
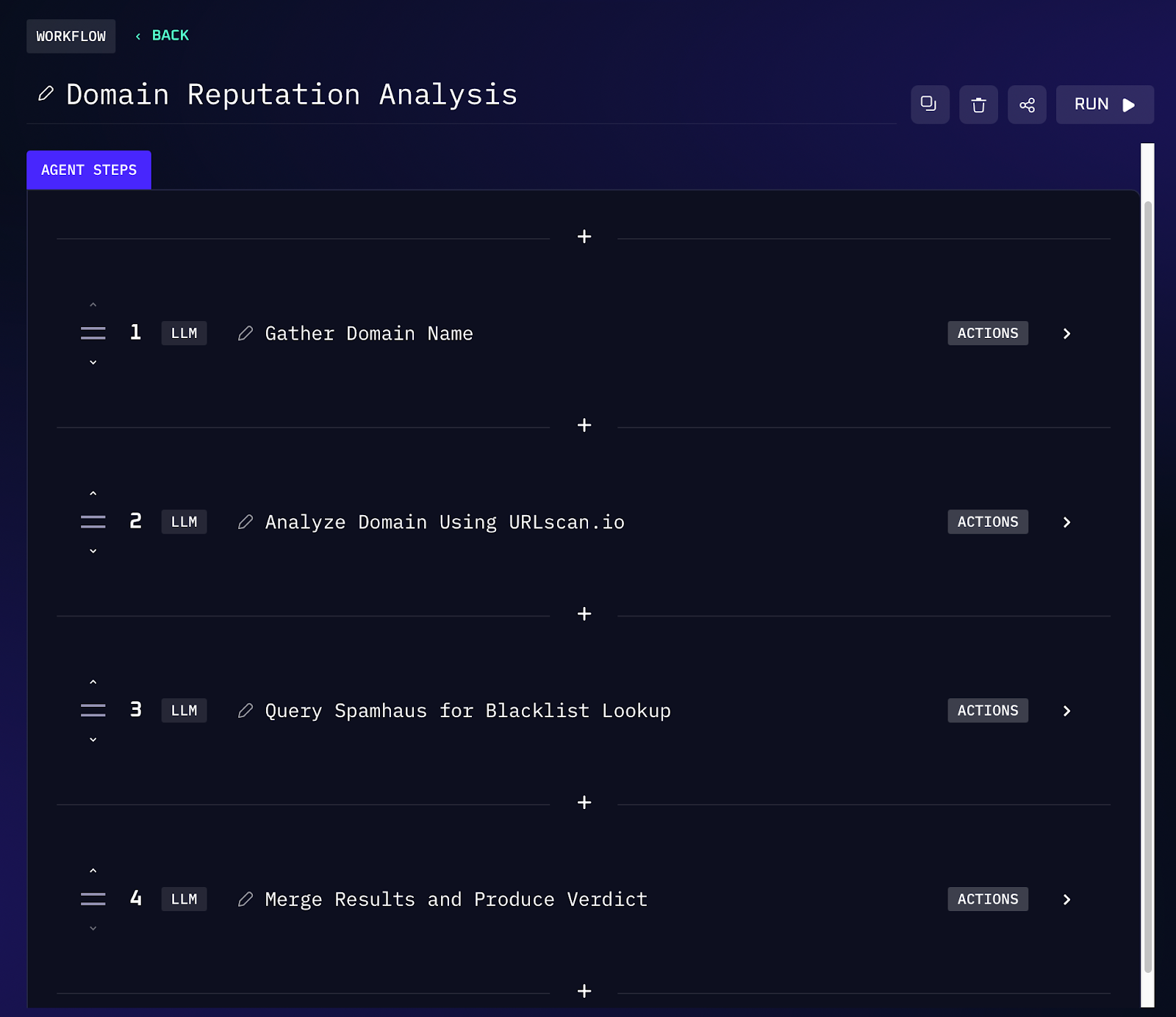
Workflow Steps (Domain Reputation Lookup)
1. An analyst supplies the domain name. This could be triggered during an investigation (checking a URL from an email) or proactively reviewing a newly registered domain.
2. The workflow submits the domain to URLscan.io via API for analysis. URLscan will retrieve the webpage and report details such as the domain’s IP hosting, retrieved HTML/JS content, screenshots of the site, and any other domains it contacts. This helps reveal if the site is live and what it might be doing (for example, loading suspicious scripts or showing a phishing login page).
3. Next, the workflow checks the domain (and its related IP) against Spamhaus’s threat intelligence databases. Spamhaus tracks known spam senders, phishing/malware domains, botnet controllers, etc., and it processes millions of domains and IPs daily to maintain up-to-date blocklists. If the domain is listed (or its IP has a bad reputation), that will be captured here.
4. The data from URLscan and Spamhaus is then combined. For instance, if URLscan showed the domain is serving a fake banking login page and Spamhaus flags the domain as malicious, the workflow notes both findings. If neither source finds anything alarming (e.g. the site just shows a blank page and isn’t on any blacklist), the domain is likely benign.
5. Finally, the workflow outputs a concise verdict or report. It might say “Domain X appears malicious (phishing page detected, on Spamhaus blacklist)” or “Domain Y is likely clean (no malicious activity observed in scan, not on any blocklists)”. This saves the analyst from interpreting raw data, the tool presents an actionable judgment along with key evidence.
Value of Automation
This automated domain check optimizes what would otherwise be a multi-step, manual process. Analysts don’t have to individually run a web scan, then go to a separate site to check reputation, the AI action pulls both in one go. The lookup friction is greatly reduced, meaning even junior analysts can quickly vet domains with confidence. By using reputable sources (like Spamhaus, which boasts an alliance that delivers unbiased, real-time domain and IP intelligence), the verdict carries weight. The automation also standardizes domain analysis: every domain is checked against the same criteria, leaving fewer gaps.
3. Executive Threat Summary Report
Security leaders and other teams benefit from a high level weekly briefing on the cybercrime ecosystem, but preparing such a report manually can eat up hours. This workflow automates the weekly threat intelligence summary by pulling data from multiple external sources and delivering a report straight to your Slack channel. It typically aggregates the top incidents, breaches, or notable threat trends from at least three sources, for example, an open source intelligence feed, a government CERT advisory feed, and a cybersecurity news RSS. The AI agent collates these inputs, filters the signal from the noise, and then generates a concise executive style summary.
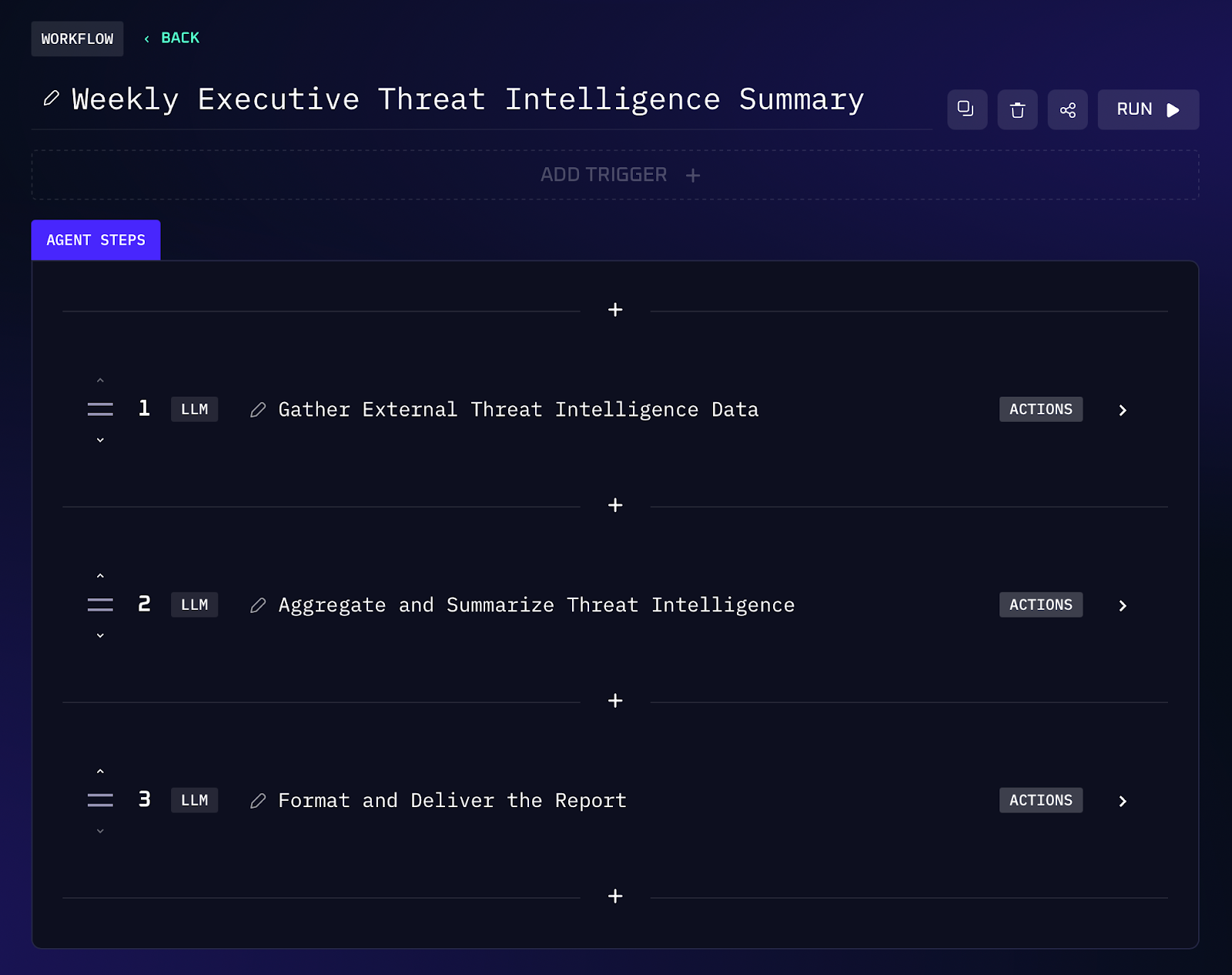
Workflow Steps (Threat Feed Aggregation & Reporting)
1. On a scheduled interval (e.g. weekly), the workflow automatically fetches data from three chosen threat intelligence sources. These could be RSS feeds or APIs of threat intelligence reports, such as industry news sites, ISAC feeds, government CERT alerts, or vendor blogs. Each feed provides recent items like breach announcements, critical vulnerabilities, or new threat actor tactics.
2. The workflow parses the collected feed data and selects the most relevant or high impact items. For instance, it might extract the top 5 incidents (e.g. a major ransomware attack, a zero-day exploit in popular software, a nation state campaign alert, etc.). It looks for trends as well, such as a pattern of attacks in a particular industry or a spike in a certain type of threat.
3. An AI summarization step then converts those raw items into a coherent report. This report is written in an executive friendly style: short descriptions of each incident, why it matters, and possibly an outlook or recommendation.
4. The content is formatted as a neat message or brief report suitable for Slack. The workflow ensures it’s in plain text or simple markup so that it’s easily readable in a chat channel. No fancy attachments needed, just the key facts in a digestible form.
5. Once the summary is ready, the workflow posts it to a predefined Slack channel (for example, #exec-threat-updates). Because this is automated, it happens at the same time every week without someone having to remember to do it.
Value of Automation
By automating the threat summary, you keep teams aligned on emerging threats without manual effort. No analyst has to spend Friday afternoon writing a report or risk forgetting to include an incident. The AI does the heavy lifting of sifting through multiple intelligence feeds (which themselves can be noisy) and shows you only the important items, ensuring that leadership’s attention is drawn to the right things.
4. Dark Web Credential Exposure Monitor
One of the scariest ways to find out about a breach is when stolen credentials for your company show up on the dark web. Rather than waiting for an incident (or a third party tip), smart security teams monitor breach databases to catch compromised accounts early. This workflow watches services like Have I Been Pwned (HIBP) and DeHashed for any credentials linked to the organization’s email domains. HIBP aggregates billions of records from data breaches; it allows domain owners to search if any email addresses from their domain appear in new breaches. DeHashed similarly indexes leaked credentials from dark web markets and paste sites. In our automated workflow, whenever a new breach dataset is published that includes any company email (e.g. @yourcompany.com), the system will detect it. It then pulls additional details, for example, which breach it was (source), the date of the breach, and what types of data were exposed (password hashes, personal info, etc.). Armed with that context, the workflow validates the findings and immediately alerts the security team so they can take action.
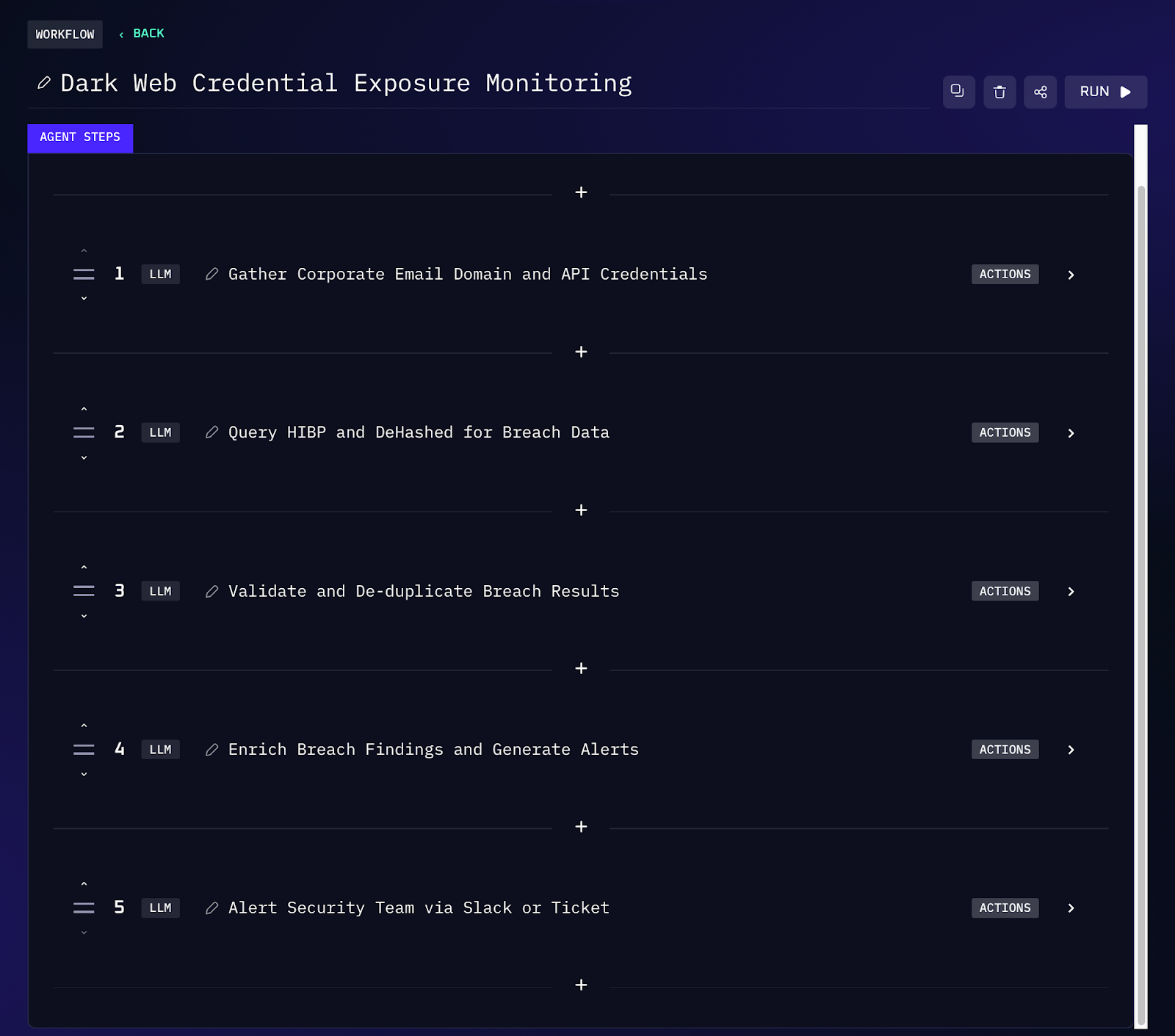
Workflow Steps (Credential Leak Monitoring)
1. The security team configures the company’s email domains (e.g. yourcompany.com) for monitoring. The workflow routinely checks these against breach data sources. HIBP offers domain monitoring features that notify when any email at the domain appears in a new breach. Similarly, the workflow can query DeHashed’s API on a schedule for any mentions of the domain in newly leaked credential sets.
2. When a trigger is detected (e.g. HIBP reports new hits or on a daily schedule), the workflow retrieves the details. For each exposed account (email address) found, it gathers data like the name of the breach (e.g. LinkedIn 2025 breach), the date it occurred, and potentially what was leaked (password, personal data, etc.).
3. The workflow cross validates the information to ensure it’s relevant. For instance, if the same credential appears via both HIBP and DeHashed, it will merge that information.
4. For each new credential exposure, the workflow attaches important context: which breach/source it came from, when that breach happened, and any available details on what data was compromised. For example, “Employee alice@yourcompany.com found in Breach X (June 2025), passwords and 2FA tokens exposed.” This enrichment helps the team assess severity (password leaked vs. just email) and urgency.
5. Finally, the system sends an alert (via email, ticket, or chat) to the security operations team with the pertinent info. It might create an incident ticket or a high priority Slack message detailing the affected accounts and recommending actions.
Value of Automation
This workflow provides peace of mind by acting as a 24/7 sentry for your identity security. Instead of relying on employees to self-report (or worse, attackers exploiting an account unnoticed), the automation assures that any credential linked to your company that leaks will be brought to light. The enrichment of breach details adds valuable context; knowing the breach source can help determine the scope and urgency. In the big picture, this kind of monitoring lowers the risk of silent compromise.
5. Ransomware Leak Site Monitor (Ransomware.live)
Ransomware gangs don’t just encrypt data, they often steal it and post the victim’s name on leak sites as extortion. Tracking these leak sites can provide early warning if a partner, supplier, or any organization you care about has been hit. However, there are dozens of ransomware groups each with their own leak websites (usually on the dark web), making manual monitoring impractical. Enter the ransomware.live feed: it’s a consolidated RSS feed that collects new victim postings from many major ransomware groups in one place. This workflow subscribes to the ransomware.live RSS and automatically monitors it for any new entries. Each time a company name is published by a ransomware gang, the workflow grabs the details, typically the victim organization’s name, the date of the leak posting, and which ransomware group is claiming responsibility. The workflow can filter for entries of particular interest (for example, companies in the same industry or geography as yours, or key suppliers’ names). It then formats the findings into an intelligence report or alert.
Workflow Steps (Ransomware Victim Tracking)
1. The workflow begins by subscribing to the master RSS feed provided by Ransomware.live. This feed consolidates disclosures from multiple ransomware gangs’ leak sites into a single stream of “new victim” events.
2. The automation regularly polls the RSS feed to check for any new entries. Each entry usually corresponds to a victim organization being listed by a ransomware group.
3. When a new feed entry is detected, the workflow parses out the important fields: the victim company’s name, the ransomware group name, and possibly the date/time or any other info in the post (some leak sites also include a small description or the type of data stolen). This data is normalized into a structured format (e.g. “Company X posted by REvil on 2025-11-01”).
4. The workflow can compile multiple new entries into a brief report or message. For instance, if several companies were listed in the last 24 hours, it can create a list of those. It formats this information clearly which ensures the intelligence is easily readable and actionable for the team.
5. Finally, the workflow automatically shares the formatted ransomware victim updates to a Slack channel. Posting it in Slack means the security team and other stakeholders see it right away, in a tool they already use.

Value of Automation
This ransomware leak monitoring provides timely intelligence on potential exposures that could otherwise fly under the radar. If a vendor or a competitor is hit by ransomware, knowing sooner allows your team to respond proactively, whether that’s shoring up defenses (in case the attack spreads or similar tactics are used against you) or contacting the third party to understand the impact. The automation here is vital because the amount of leak sites is constantly changing and expanding; a human would struggle to keep track of even a fraction of it.
Take Your Next Steps With Kindo
Threat intelligence doesn’t have to be manual, fragmented, or slow. With Kindo.ai, your team can orchestrate enrichment, monitoring, and reporting from a single chat interface while staying focused on what matters most.
Book a demo to see how Kindo transforms repetitive threat intelligence tasks into instant automated actions that keep your SecOps team informed, proactive, and ahead of the curve.



